This Scenario Best Describes Which Network Function
Communicate with the UE store its subscription and credentials allow access to external networks services provide security and manage the network access and mobility. Standard operating procedure B.
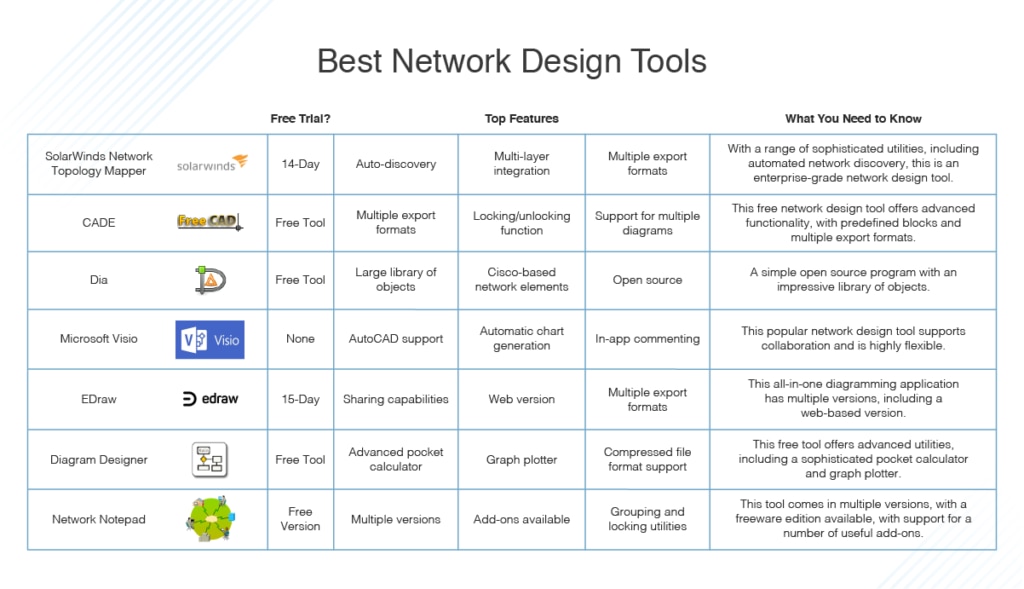
7 Best Network Design Tools How To Design A Network Dnsstuff
For that it uses the contexts each consisting of some data types and their transfer syntaxes.
. All nodes k such that ki is an arc of the network. A student is playing a short web-based movie with sound. Analyze the following scenarios and determine which accurately describes the use of an ad hoc Wi-Fi network.
Describe the VPN technology and explain why it is the best choice for Corporation Techs. It is this particular structure that we shall exploit in. This of course is not surprising as the network always has to carry out some basic functions such as.
What is the type of attack the cyber criminal launches. SDN is an architecture that separates the network control and. Scenarios for resilient leaders published by Deloitte and Salesforce.
This is a great opportunity to leave a strong impression on the hiring manager and show them youre the best fit for the job. It verifies confidentiality of files. Which of the following BEST describes this process.
450 questions andor answers were updated by Rachelle Enns on March 16th 2022. Best practices in implementing virtualization Introduction Virtual environments are different than physical environments Potential usage scenarios and best practices Obtaining maximum return on virtualization Best practices in systems automation About the author. In an iterative process users engineers and designers communicate through the use of scenarios.
Interview questions and answers were first added on June 29th 2018. Press Ctrl F in the browser and fill in whatever wording is in the question to find that questionanswer. It is used to decode files.
Azure Functions lets you use keys to make it harder to access your HTTP function endpoints. The use of scenarios is an effective way to describe concrete working practices. The unique identifier burned into the phone is a.
Both likely scenarios and unlikely worst-case events. To fully secure your function endpoints in production consider implementing one of the following Function app-level security options. The objective function summation is over arcs i j that.
The unique identifier burned into the phone is a transport layer address used to contact another network device on the same network. A common scenario of a network-flow problem arising in industrial logistics concerns the distribution of a. The functions of the presentation layer are as follows.
Emerging Network Technologies Exam Answers. Choose a real work-related situation. Run Setupexe from your Windows product DVD or network share.
Together we explored a. A user facing a tight deadline at work experiences difficulties logging in to a network workstation so the user activates a smartphone hotspot and connects a personal laptop to save time. 5 Tips for Your Answer.
Interview questions and answers were updated by Rachelle Enns on an unknown date. It provides the users with a way to execute the session service primitives. Create a professional SSLTLS VPN.
This scenario consists of the following stages. A student is using a classroom VoIP phone to call home. They are part of a protest group behind a political cause.
The transport layer ensures the correct web page is delivered to the correct browser window. Scenario-based and situational interview questions assess your values and work ethics so make sure you consider your answers carefully TIP 2 More often than not the type of scenarios you will be presented with during your job interview will assess whether or not you are a team player and also whether or not you look to put the. A cyber criminal sends a series of maliciously formatted packets to the database server.
Completely describes the physical layout of the network. Turn on App Service authentication and authorization for your Functions app. It is used as a key for encryption.
If the question is not here find it in Questions Bank. Which term describes evidence that is in its original state. After every test scenario is implemented testers should be able to confidently say that they can answer every single question about that particular feature or function.
It helps identify malware signatures. CompTIA Network Exam. Which statement best describes a motivation of hacktivists.
A student has two web browser windows open in order to access two web sites. The server cannot parse the packets and the event causes the server crash. Best Practices to Create Test Scenarios.
Create one test scenario for a single requirement or user story for simplicitys sake. Which scenario describes a function provided by the transport layer. Two or more wireless devices connect to each other on a temporary basis.
Your report will include details for all relevant information persuasive justification for your recommendations and methods to measure the success of each major network enhancement. Scenario analysis is the process of estimating the expected value of a portfolio after a given change in the values of key factors take place. Our Update History for Scenario Based.
Corroborating evidence Best evidence Indirect evidence Direct evidence How is the hash value of files useful in network security investigations. When a session is established the peer entities negotiate for one or more contexts. The most common scenario for Windows Setup is performing a custom installation.
Checked for grammar and spelling mistakes by Crystal Goines on March 16th 2022. Create a network diagram that includes. The best approach is to take a challenging difficult experience and use it to show your emotional intelligence and your work experience.
Which scenario describes a function provided by the transport layer. CCNA 3 v7 Modules 13 14. The request is approved and the port is opened.
What are the two most effective. A student is using a classroom VoIP phone to call home. In this scenario you install Windows onto a computer that does not have an operating system or has a previous version of Windows.
CompTIA Network Exam Practice Questions Sample N10-007 Question479. Pick the phrase that best describes Software Defined Networking SDN Answers. The culmination of this collaboration is presented in The world remade by COVID-19.
Greg Shields is an independent writer speaker and IT consultant based in Denver. This leads to the assumption that there is a difference between the description of work processes by the care management and the everyday work 112113.

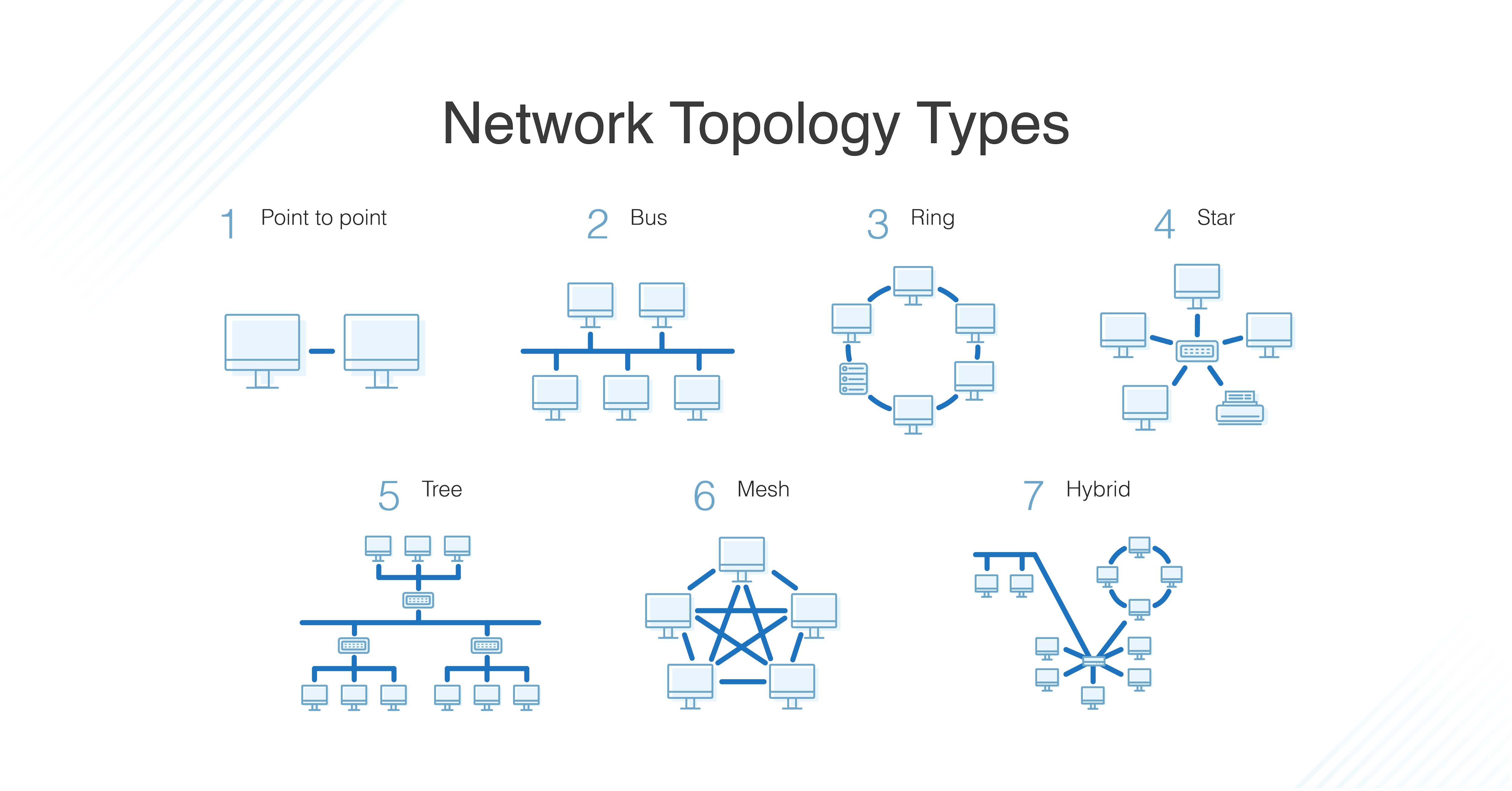
6 Best Network Topologies Explained Pros Cons Including Diagrams
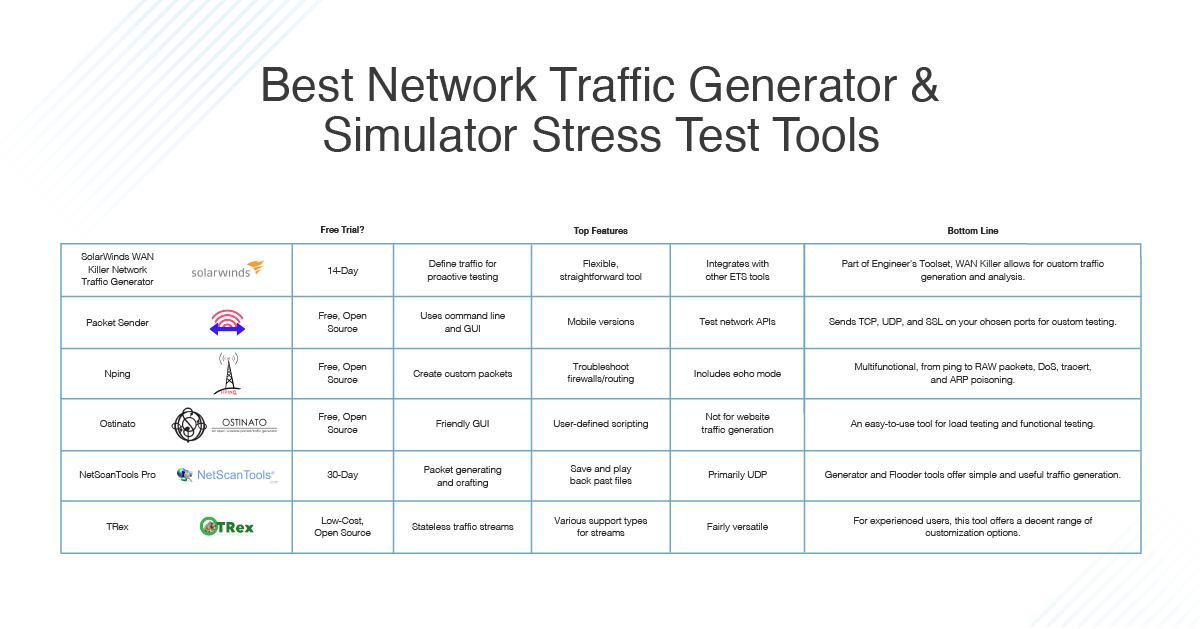
6 Best Network Traffic Generator And Simulator Stress Test Tools Dnsstuff

What Is Network Topology Best Guide To Types Diagrams Dnsstuff
No comments for "This Scenario Best Describes Which Network Function"
Post a Comment